Endpoint access control
Is possible restrict access to any endpoint.
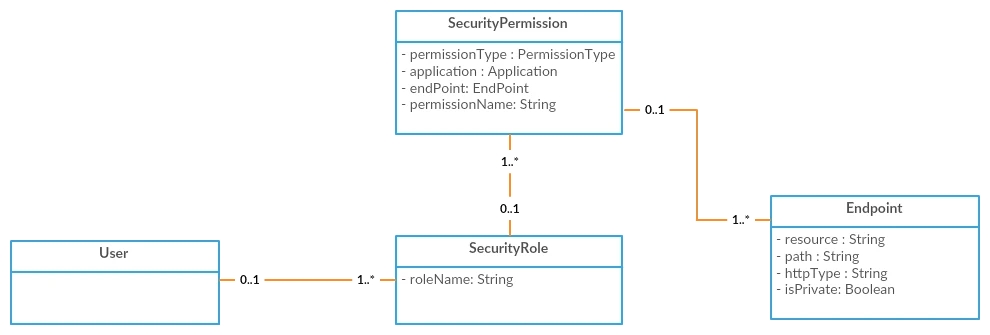
In order for a user to get access to a given API Endpoint, the user must belong to a SecurityRole that has a SecurityPermission for the API Endpoint.
he endpoint access control is done also against the objects requested using the fields JSON in the HTTP Header. So for instance if the endpoint Vessel.GET is present and the user does not belong to a SecurityRole that has a SecurityPermission for the Vessel.GET endpoint, requesting the Voyage resource specifying the following JSON in the fields parameter will get unauthorized (HTTP 401):
If the same user requests with the following JSON, it will get access because vesselName attribute is part of the minimal view of Vessel resource:
The same access control is performed when a WebhookSubscription is requested. If the user tries to subscribe for an object that has an Endpoint in the system, the subscription will be created only if the user can access to the Endpoint, otherwise Bad request (HTTP 400) exception will be thrown.
To create a new Endpoint it has to be used the endpoint /ws/rest/Endpoint posting a JSON like this:
To create a new SecurityPermission it has to be used the endpoint /ws/rest/SecurityPermission posting a JSON like this:
To create a new SecurityRole. Post the following JSON to /ws/rest/SecurityRole:
To add a SecurityPermission to a SecurityRole. Post the following JSON to /ws/rest/SecurityRole:
To add a SecurityRole to a User. Post the following JSON to /ws/rest/SecurityRole:
Was this helpful?